What is an IT Health Check, and why is it important?
An IT Health Check (ITHC), also known as a Penetration (Pen) Test, is an important component in the over-arching Security Assurance activities and one of several possible mechanisms used to provide confidence and assurance of the security baseline design.
An ITHC is a series of controlled ethical hacking tests and actions designed to deliberately identify and expose security vulnerabilities that might be present in IT solutions. The objective of scrutinising an IT solution in this manner allows the project and business teams to understand the risk exposure should it become compromised and formulate a remediation plan to mitigate and protect the systems and data that might reside in it.
When should an ITHC be considered?
There are 3 primary scenarios when an ITHC might be undertaken:
Introduction of new IT services
An ITHC at this phase of a project life cycle helps to establish the security baseline before the solution is made available for wider use. It provides the ability to act on any risks and issues identified whilst in a safe environment and reduces impact on others (users as well as systems) overall.
Changes to an existing IT baseline
Any major design change to an existing IT service should include a review for a new ITHC to determine that the baseline change does not introduce security risks. ITHC’s are normally performed prior to formal release/rollout of the changes being made and therefore identification and mitigation plans can be established and undertaken in a safe environment.
Scheduled ITHC for existing IT services
As technology continues to evolve, it is important to understand the impact that this might have on existing solutions. Therefore, is it recommended that Product and Service owners work with the CAT Team (Cyber Assistance Team) to review existing IT solutions and plan to undertake an ITHC on an agreed schedule. This helps to re-assess the security baseline, remediate any risks and issues as agreed, and therefore provide ongoing protection of systems and data.
What can be tested?
The ITHC is performed by highly trained pen testing specialists, and (typically) by an external 3rd party ITHC service provider.
There are many types of penetration tests that can be applied, including but not limited to:
-
Network and host configuration
-
Web application
-
Wireless network
-
Client-server application
-
End User devices such as laptops or mobile phones
-
Social engineering
-
Build configuration
Cloud Platforms
If the application or service you intend to test is hosted within a cloud platform service offering, such as Azure and AWS (Amazon Web Service), there are Rules of Engagement that you should be aware of. Information can be found for the following:
- Microsoft Azure: https://www.microsoft.com/en-us/msrc/pentest-rules-of-engagement
- AWS: https://aws.amazon.com/security/penetration-testing/
Further to this, the MoJ AWS Cloud Platform Team have produced additional guidance that can be accessed here: https://user-guide.cloud-platform.service.justice.gov.uk/documentation/other-topics/security-testing-and-ithc.html#security-testing-and-ithc
Vulnerability Scanning
A vulnerability scan is not the same as an ITHC however, it can be performed and used to help build on the overarching story of the product being tested.
A vulnerability scan is automated and is entirely software whereas an ITHC is conducted by trained, qualified professionals, and uses human interaction and human ingenuity to discover flaws that automated tools often miss.
Further information and guidance about vulnerability scanning can be found here: https://security-guidance.service.justice.gov.uk/vulnerability-scanning-guide/#roles-and-responsibilities.
Primary Points of Contact
The Cyber Assistance Team (CAT) Consultants are the primary points of contact for projects and Product/Service owners. The Consultants will work with the team to help ascertain the ITHC requirement and scope, as well as any forward schedule for ongoing ITHC requirements. You can contact the CAT Team directly to request Consultation support if one is not already working with your project already:
CyberConsultancy@digital.justice.gov.uk
How can I book an ITHC?
If you have a requirement to conduct an ITHC on your network and/or application, please complete and submit the New ITHC Request form:
The Cyber Security, Privacy and Live Service Delivery Team manage the engagement and planning coordination between yourself and the 3rd party ITHC Team. If you have any queries, you can contact the team via:
Governance, workflow and timeline considerations
Timeline Consideration
It is recommended that an approximate timeline of 8 weeks is considered in your project plan to enable the planning and undertaking of the ITHC. Maturity, size, and complexity of the scope will influence this.
Scope Changes
Changes to scope can be reviewed and considered. However, there is a risk that this will affect delivery dates, ITHC Provider availability, and end quote price.
In scenarios where the formally agreed test dates are impacted, charges might be incurred for delays and cancellations.
It is strongly recommended that ITHC scope is understood and confirmed as much as possible, and prior to submission.
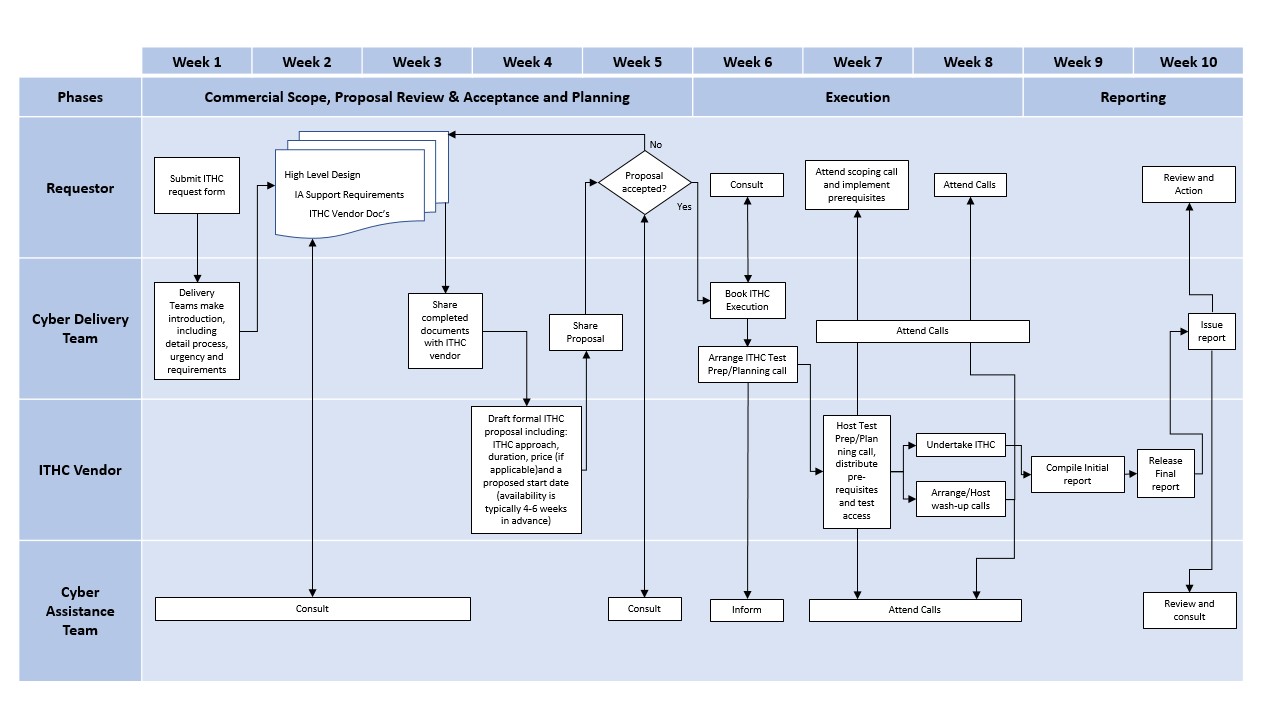
The following workflow aims to provide an overview as to the primary roles and action owners involved in the ITHC process:
How to reach us
Should you have any further queries about the ITHC process then please don’t hesitate to contact the Cyber Security, Privacy, and Live Service Delivery Team: